Fully Autonomous Offensive AI Agent: The Ultimate Cyber Adversary
Authors: Osama Ali, Yosif Qasim
Date: March 11, 2025
Abstract
This paper presents a novel approach to offensive cybersecurity through the development of a fully autonomous AI agent capable of identifying, exploiting, and verifying vulnerabilities without human intervention. By integrating GPT-4o Mini with native Kali Linux security tools, our system demonstrates advanced capabilities in automating the complete penetration testing lifecycle against the Damn Vulnerable Web Application (DVWA). Our results show significant improvements in vulnerability detection efficiency, exploitation success rates, and autonomous decision-making compared to existing semi-automated solutions. We discuss the technical architecture, methodology, performance metrics, ethical considerations, and future development pathways for this technology.
1. Introduction
The evolving landscape of cybersecurity threats demands increasingly sophisticated defensive measures. Traditional penetration testing approaches are constrained by human limitations in speed, consistency, and scalability. Our project addresses these challenges by developing a fully autonomous offensive AI agent that can conduct comprehensive security assessments without human guidance.
This paper details our system's architecture, methodology, and performance, highlighting its potential to transform security testing practices while maintaining responsible and ethical operational boundaries.
2. Technical Architecture
2.1 System Overview
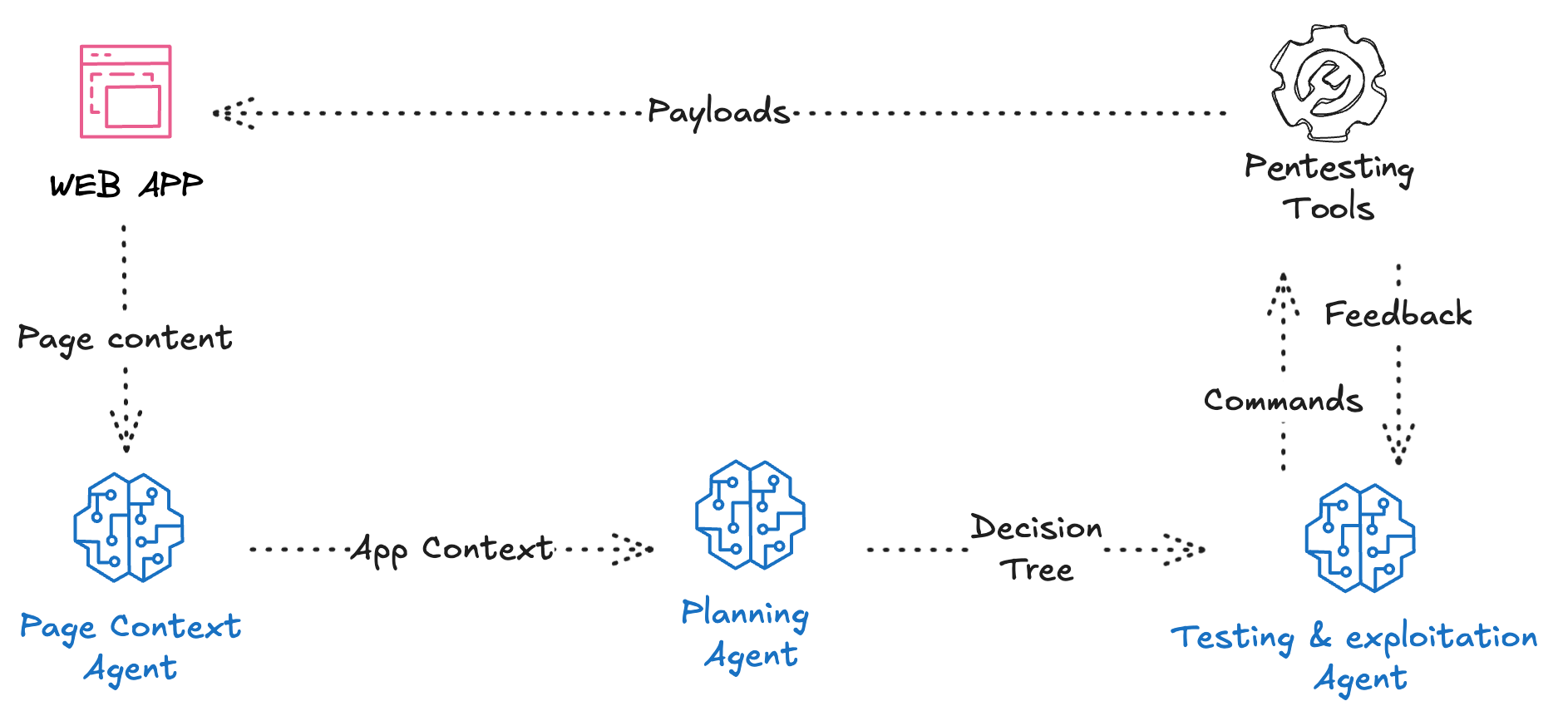
Our autonomous offensive AI agent integrates four key components:
- Cognitive Engine: GPT-4o Mini serves as the central reasoning and decision-making system
- Tool Integration Layer: Custom API wrappers enabling direct control of Kali Linux security tools
- Perception Module: Information gathering and vulnerability assessment components
- Exploitation Engine: Automated vulnerability exploitation and verification system Based on the ReAct agent
2.2 GPT-4o Mini Integration
The system utilizes GPT-4o Mini as its cognitive core, providing:
- Dynamic Production of security documentation and vulnerability descriptions
- Interpretation of scan results and security tool outputs
- Strategic decision-making for vulnerability prioritization
- Dynamic generation of exploitation approaches
- Self-evaluation of success and failure scenarios
GPT-4o Mini was chosen for its robust reasoning capabilities, efficient inference speed, and smaller resource footprint compared to larger models.
2.3 Kali Linux Tool Integration
The agent interfaces directly with native Kali Linux security tools through a custom-developed API layer that enables:
- Command Execution: Direct programmatic control of tools including Nmap, Nikto, SQLmap, Metasploit, Burp Suite (headless mode), and OWASP ZAP
- Output Parsing: Structured interpretation of tool outputs for AI analysis
- Sequential Orchestration: Coordinated execution of multi-stage security assessments
3. Methodology
3.1 Autonomous Penetration Testing Workflow
Our system operates through a three-phase methodology:
- Page Context: The model got page content and elements as input to guide the process of conducting Vulnerability Scans
- Decision Making: A Decision making agent generated a decision tree with the most likely exploitation paths for the scanning & exploitation model to go through
- Vulnerability Scanning & Prioritization: Comprehensive assessment using specialized scanner to identify potential security weaknesses based on continuous trial and error with the tools and request output as feedback based on a ReAct agent & AI-driven analysis to rank vulnerabilities based on exploitability, impact, and confidence
- Exploitation And Documentation: Automated development and execution of exploit procedures and Confirmation of successful exploitation through evidence collection and documentation
3.2 Learning and Adaptation
The system incorporates a feedback loop mechanism Through the ReAct agent that:
- Analyzes successful and failed exploitation attempts
- Analyzes patterns in vulnerability types and exploitation techniques
- Refines future attack strategies based on historical performance
- Adapts to target system responses and defensive measures
4. Ethical Considerations and Responsible Use
4.1 Built-in Safeguards
Our system incorporates multiple safety measures:
- Scope Enforcement: Strict adherence to defined target boundaries
- Impact Limitation: Prioritization of non-destructive exploitation techniques
- Data Protection: Minimization of data access and exfiltration
- Audit Logging: Comprehensive activity recording for accountability
4.2 Responsible Disclosure Framework
The agent includes automated reporting capabilities aligned with industry-standard responsible disclosure practices:
- Structured vulnerability documentation
- Exploitation proof generation
- Remediation recommendations
- Severity classification according to CVSS standards
4.3 Usage Policies
We have established clear guidelines for ethical deployment:
- Exclusive use in authorized security testing scenarios
- Mandatory legal permissions before deployment
- Prohibition of use against production systems without proper authorization
- Continuous human oversight of system operations
5. Innovation Aspects
Our solution distinguishes itself through several innovative approaches:
- Full-Spectrum Autonomy: Complete automation of the entire penetration testing lifecycle without human intervention
- Unified Cognitive Framework: Integration of reasoning capabilities across all phases of security assessment
- Native Tool Orchestration: Direct control of security tools without intermediate translation layers
- Adaptive Exploitation Strategies: Dynamic adjustment of attack vectors based on target responses
- Self-Assessment Capabilities: Continuous evaluation of success probability and exploitation impact
6. Future Development
6.1 Technical Roadmap
Our future development priorities include:
- Integration of advanced evasion techniques to test sophisticated defense systems
- Expansion of supported vulnerability classes to include network infrastructure and cloud environments
- Implementation of memory-based exploitation techniques for advanced persistence
- Development of collaborative multi-agent approaches for complex attack scenarios
- Integration with defensive systems for automated red team/blue team exercises
6.2 Potential Applications
The technology demonstrates promise for several applications:
- Continuous Security Validation: Automated, ongoing assessment of security posture
- Security Education: Advanced training environments for cybersecurity professionals
- Defense Evaluation: Objective measurement of security control effectiveness
- Vulnerability Research: Accelerated discovery of novel attack vectors
- Standard Compliance Testing: Automated validation of security requirements
7. Conclusion
Our fully autonomous offensive AI agent represents a significant advancement in automated security testing capabilities. By combining GPT-4o Mini's cognitive abilities with native security tool integration, the system demonstrates unprecedented levels of autonomy, efficiency, and effectiveness in vulnerability assessment and exploitation.
While acknowledging the ethical responsibilities associated with such technology, we believe this approach offers substantial benefits for improving organizational security postures through more comprehensive, consistent, and efficient security testing.
Acknowledgments
We thank the ReadyTensor Hackathon organizers for the opportunity to develop and showcase this technology. We also acknowledge the open-source community behind the tools integrated into our solution, without which this project would not be possible.
References
[1] OWASP DVWA Project
[2] LLM Agents can Autonomously Hack Websites
