Security Operations Centers (SOCs) rely on accurate interpretation of system signals, logs, and operational context to detect potential threats. Traditional single-agent LLM workflows struggle with tool grounding, evidence separation, and reasoning reliability.
This project presents Cybersecurity Monitor, a modular multi-agent system that simulates a SOC-style analysis pipeline. Multiple agents collaborate through a structured orchestration layer to collect evidence, analyze security signals, and generate a grounded final security report. The system uses Model Context Protocol (MCP) for tool integration, LangGraph for agent orchestration, and DeepEval for formal evaluation of reasoning quality.
Security analysis is inherently multi-step and role-driven:
Single-agent workflows often blur these boundaries, increasing hallucination risk. This project demonstrates how a multi-agent architecture with explicit role separation improves reliability, transparency, and extensibility in security analysis tasks.
The Cybersecurity Monitor system is composed of four primary layers:
Each layer is loosely coupled, allowing independent extension and testing.
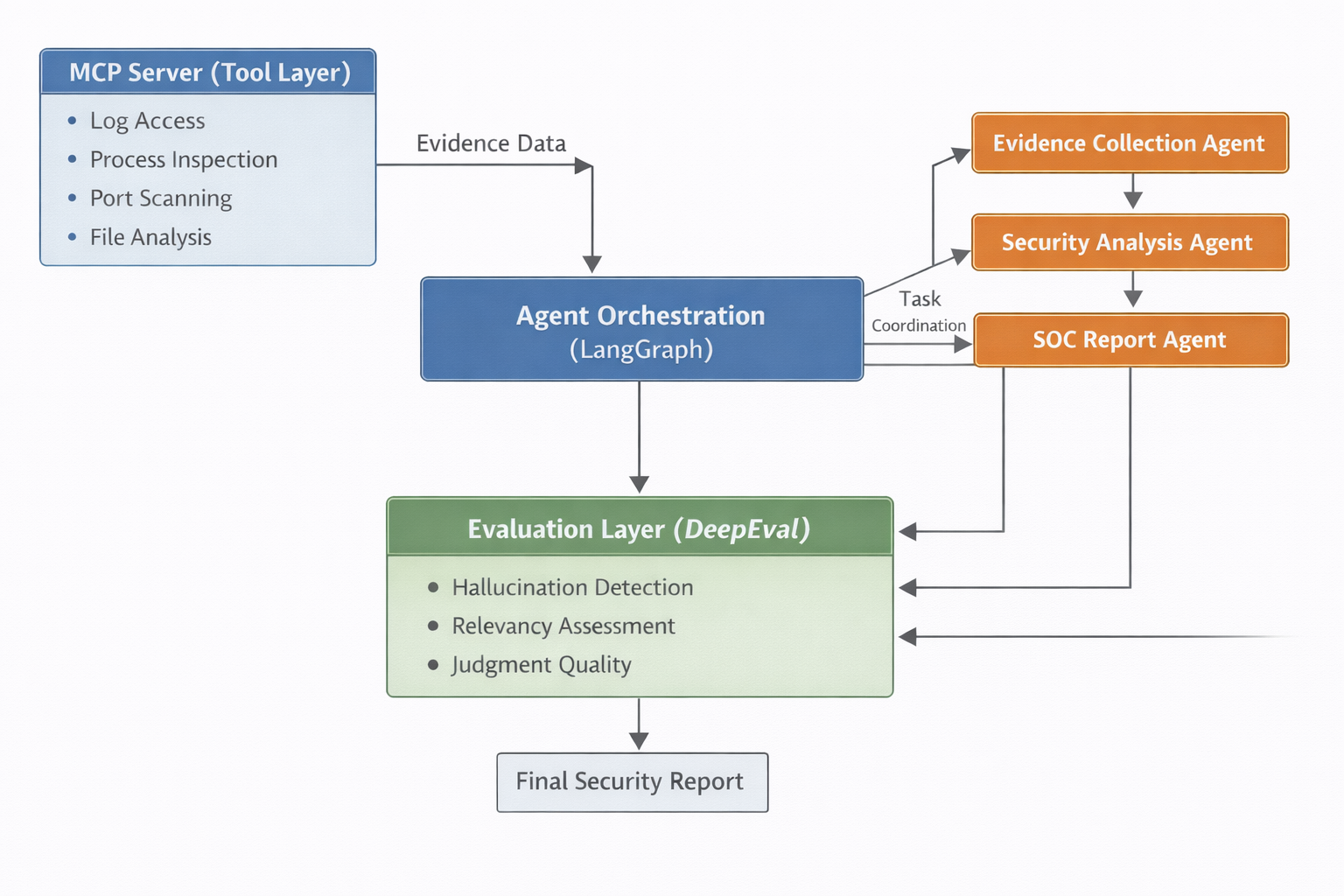
The MCP server exposes controlled system-level tools to agents, including:
All tools return structured outputs and act as the only source of ground truth. Agents are not allowed to reason beyond tool-provided data.
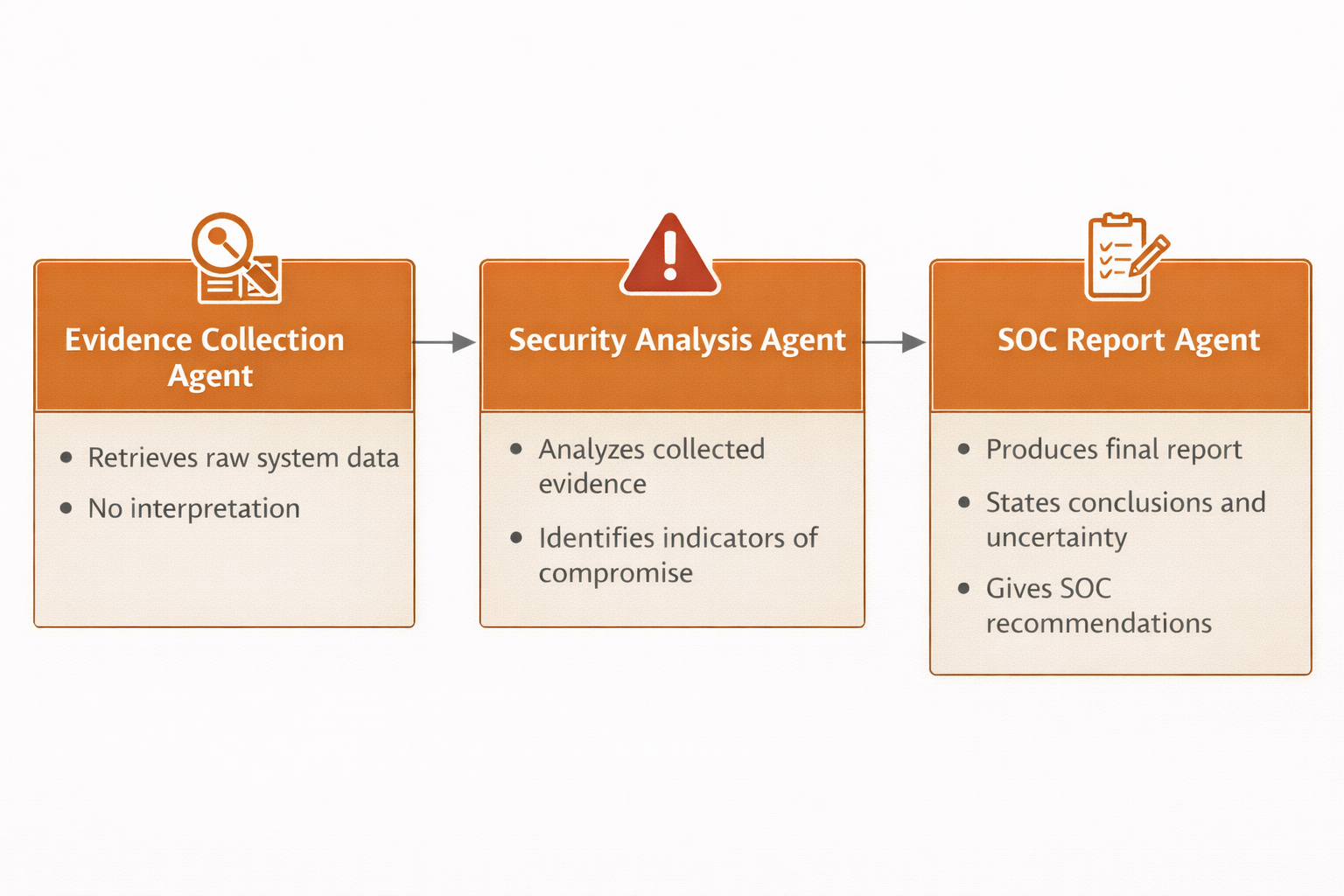
The system consists of at least three agents, each with a distinct role:
This separation enforces clean reasoning boundaries and reduces hallucination.
LangGraph is used to define:
Typical execution flow:
Evidence Collection → Security Analysis → SOC Report
This orchestration design allows easy insertion of:
The system integrates multiple tools using the Model Context Protocol:
Each tool:
This approach makes the system extensible and secure while maintaining strict evidence grounding.
To ensure reliable reasoning, the project includes an automated evaluation layer using DeepEval.
Tests are executed using pytest and invoke the full agent pipeline end-to-end.
A typical system output follows SOC reporting conventions:
=== FINAL SECURITY REPORT ===
Event Analysis:
No confirmed malicious activity detected based on available system signals.
Indicators of Attack:
None identified.
Assessment:
Current evidence is insufficient to assert compromise.
Recommendations:
- Continue monitoring system logs
- Perform scheduled security scans
- Review network traffic periodically
The architecture is designed for incremental expansion. Planned future enhancements include:
All future tools will be added as new MCP endpoints without changes to agent logic.
The repository includes:
.env and .env_exampleDetailed instructions are provided in setup.md and usage.md.
Cybersecurity Monitor demonstrates how multi-agent collaboration, tool grounding, and structured orchestration lead to more reliable security analysis than single-agent workflows. By combining MCP, LangGraph, and formal evaluation, this project provides a strong foundation for scalable and extensible SOC automation systems.