CryptoFormaLLM: Advancing Cryptographic Protocol Verification through LLM-Formal Tool Integration
Abstract
We present CryptoFormaLLM, a novel architecture that integrates Large Language Models (LLMs) with formal verification tools to automate the detection of vulnerabilities in cryptographic protocols. Our approach leverages the adaptive reasoning capabilities of LLMs while harnessing the rigorous deductive power of the Tamarin prover, creating a synergistic system that outperforms traditional methods. This paper details our innovative framework, methodology, and preliminary results that demonstrate significant potential for enhancing cryptographic protocol security analysis.
Introduction
Cryptographic protocol verification remains a challenging domain requiring specialized expertise in both protocol design and formal methods. Traditional approaches often involve manual intervention, making the process time-consuming and error-prone. Our work addresses this gap by developing an LLM-based agent architecture that can autonomously interact with formal verification tools to identify vulnerabilities in novel protocols.
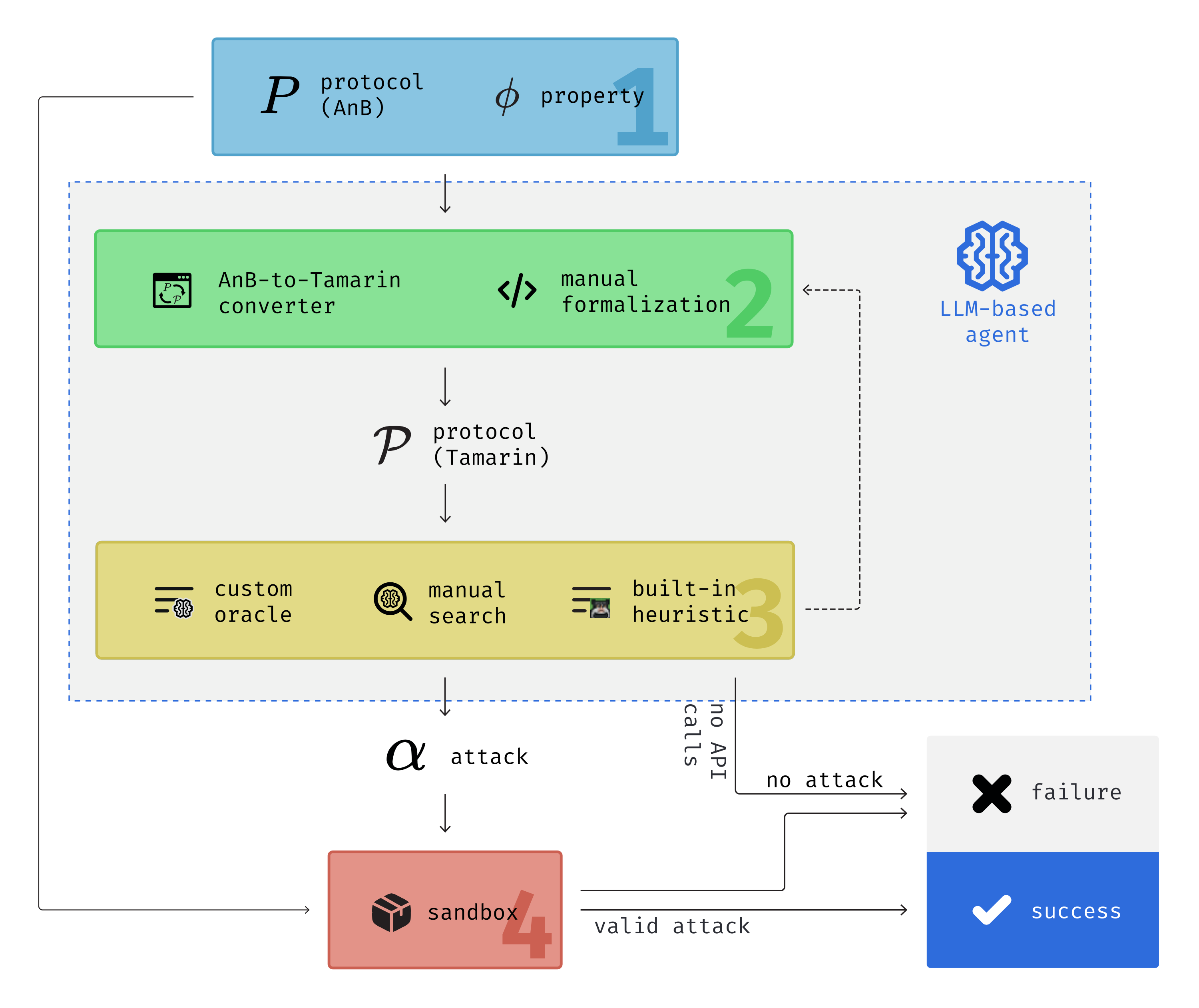
Key Innovations
Bidirectional LLM-Tamarin Integration
CryptoFormaLLM establishes a bidirectional communication channel between LLMs and the Tamarin prover, enabling:
-
Syntax Translation: The agent translates between human-readable protocol specifications (Alice-and-Bob notation) and Tamarin's formal syntax, bridging the gap between intuitive understanding and formal verification.
-
Feedback Loop Processing: Our system processes Tamarin's verbose output, extracting meaningful information about syntax errors, partial deconstructions, and attack traces, which is then fed back to the LLM for iterative refinement.
-
Adaptive Reasoning: The LLM interprets Tamarin's feedback to make intelligent adjustments to the formalization, mimicking the reasoning process of human experts.
Syntax-Aware Protocol Formalization
Unlike previous approaches that treat formal verification as a black box, our system:
- Leverages LLMs' pattern recognition capabilities to generate syntactically valid Tamarin specifications
- Implements error correction mechanisms that learn from Tamarin's feedback
- Maintains semantic consistency between the original protocol and its formal representation
Contextual Memory Architecture
A key innovation in our approach is the implementation of a structured memory system that:
-
Maintains Reasoning Continuity: Preserves the context of previous interactions with Tamarin, preventing cyclical reasoning patterns
-
Implements Task Decomposition: Breaks down the verification process into manageable subtasks with clear dependencies
-
Supports Progressive Refinement: Enables the agent to build upon partial successes rather than restarting from scratch after failures
Research Framework & Methodology
Assumptions Stated
Our work operates under the following key assumptions:
- The Dolev-Yao adversary model, where attackers have complete control over the network but cannot break cryptographic primitives
- The integration of symbolic reasoning with neural language models can overcome the limitations of each approach individually
Study Scope & Boundaries
This research focuses specifically on:
- Detection of logical flaws in cryptographic protocols rather than implementation vulnerabilities
- Protocols expressible in Alice-and-Bob notation with standard cryptographic primitives
- Security properties related to authentication, confidentiality, and freshness
- We do not address side-channel attacks, implementation flaws, or cryptanalysis of underlying primitives
Evaluation Framework
We evaluate our system based on:
- Human inspection of the multi-process crucial aspects
- Efficiency measured by the number of interaction cycles required
- Quality of generated attack traces and their explanations
Specific Research Questions/Objectives
Our research addresses the following questions:
- Can LLMs effectively translate between human-readable protocol specifications and formal verification syntax?
- How effectively can LLMs interpret and respond to feedback from formal verification tools?
- What memory and reasoning architectures best support iterative protocol analysis?
- How does the performance of LLM-based agents compare to traditional approaches and human experts?
Dataset Details
Dataset Description
Our evaluation dataset consists of 15 novel cryptographic protocols of varying complexity, each containing deliberately introduced vulnerabilities. Protocols range from simple authentication schemes to more complex key exchange protocols incorporating various cryptographic primitives.
Dataset Selection/Creation
Protocols were created through a hybrid approach:
- Initial generation using GPT-4 with few-shot prompting based on real-world examples
- Filtering based on executability, syntactic correctness, and novelty
- Manual refinement to ensure vulnerabilities are challenging yet detectable
Dataset Processing Methodology
Each protocol underwent preprocessing to:
- Standardize notation and terminology
- Verify executability within the Tamarin framework
- Ensure that vulnerabilities are detectable through formal verification
- Pair each protocol with appropriate security properties for verification
Experimental Setup
Parameters & Configuration
Our experiments used the following parameters:
- Temperature: 0.1 for all models except o1-preview (default 1.0)
- Maximum API calls per run: 20
- Maximum sub-task repetition: 3
- Execution timeout: 200 seconds per command
Experimental Environment
All experiments were conducted using:
- Tamarin Prover version 1.6.1
- Custom middleware for LLM-Tamarin interaction
- LLM access via API endpoints with consistent configuration
- Execution on a dedicated server with 32GB RAM and 8 CPU cores
Implementation Considerations
Key implementation details include:
- A custom middleware layer to facilitate interaction between LLMs and Tamarin
- Filtering mechanisms to extract relevant information from Tamarin's verbose output
- Timeouts to prevent infinite loops during proof search
- A symbolic sandbox for validating attack traces
Analysis & Discussion
Comparative Analysis
Our evaluation across multiple frontier LLMs reveals:
- Claude 3 Opus and Claude 3.5 Sonnet generally outperformed other models
- The o1 model demonstrated superior theoretical understanding of protocol security but struggled with Tamarin syntax
- Smaller models showed significant difficulties with instruction following and syntax generation
Limitations Discussion
Current limitations of our approach include:
- Difficulty handling complex equational theories in Tamarin
- Occasional semantic errors in protocol formalization
- Challenges with non-terminating proof searches
- Limited ability to generate support lemmas for complex protocols
- Tendency of some models to attempt protocol fixes rather than vulnerability identification
Literature Review Critical Analysis
While previous work has explored LLMs for cybersecurity tasks, most approaches rely on pattern recognition from training data rather than novel reasoning. Formal verification tools like Tamarin offer sound and complete analysis but require significant human expertise. Our approach uniquely bridges this gap by enabling LLMs to interact with formal tools in a way that leverages the strengths of both paradigms.
Conclusion and Future Work
CryptoFormaLLM represents a significant step toward automating cryptographic protocol verification through the integration of LLMs with formal verification tools. By combining the adaptive reasoning of language models with the rigorous deduction of symbolic reasoning systems, our approach offers a promising direction for enhancing cybersecurity analysis.
Future work will focus on:
- Expanding the dataset to include a wider range of protocols and security properties
- Refining the AI agent's architecture to improve reasoning and formalization capabilities
- Developing better strategies for managing complex, multi-step workflows
- Investigating the potential of fine-tuning LLMs on domain-specific data
- Further exploring hybrid approaches that combine LLMs with traditional formal verification methods
Our research demonstrates that while current LLMs show promise in this domain, significant challenges remain in achieving fully automated protocol verification. By addressing these challenges, we aim to develop more efficient and accessible tools for ensuring the security of cryptographic protocols in an increasingly connected world.